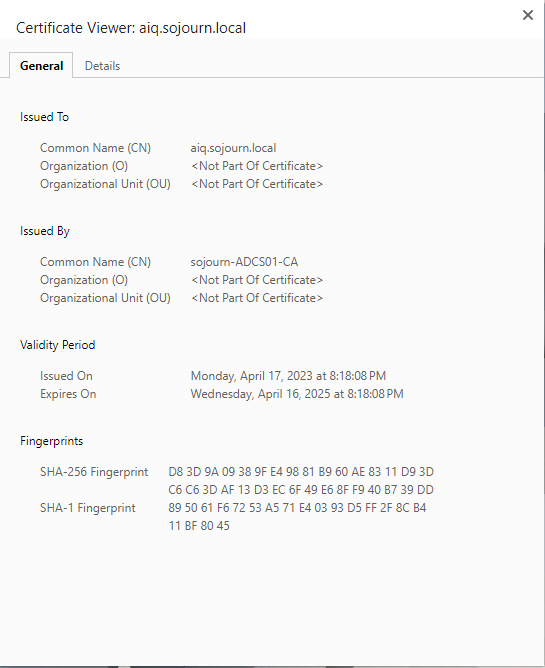
SSL Certificates and NetApp ActiveIQ Unified Manager
I am not sure when it happened but at some point, Chrome stopped me from just ignoring that some of my SSL certificates was insecure.
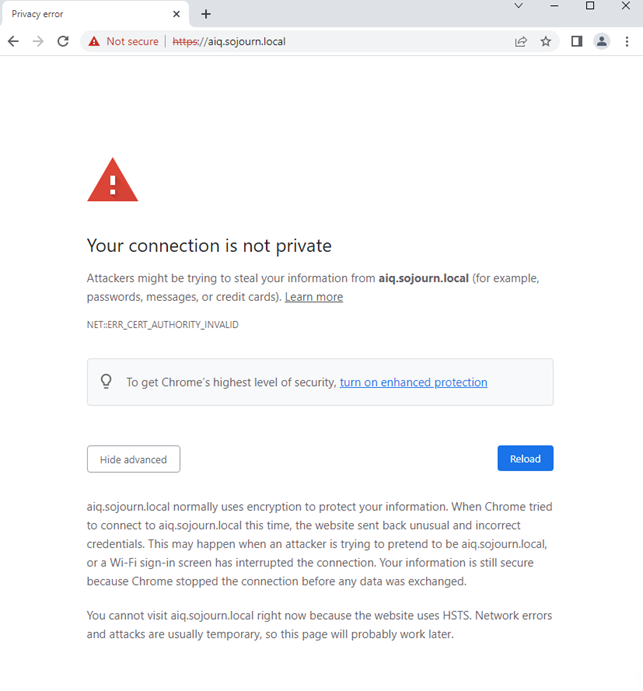
It would no longer allow me to “continue anyway”. I could just switch to Firefox or change the security settings in chrome. The correct solution is to create a signed certificate for ActiveIQ, and since it was so much “fun” to do it for System manager I decided to also do it here.
Generate the certificate
AIQ supports creating a signing request, but if you prefer you can create it manually.
This is how my HTTPS Certificate page looks in AIQ when using the default self-signed
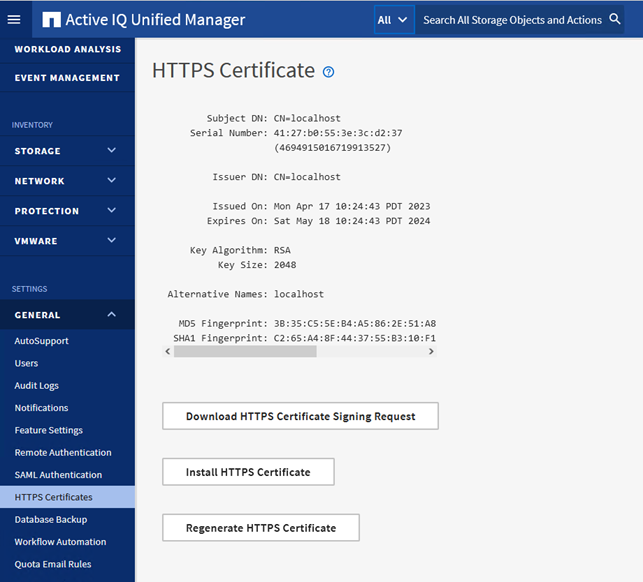
I decided to try using the signing request as it sounded easier than creating the certificate manually.
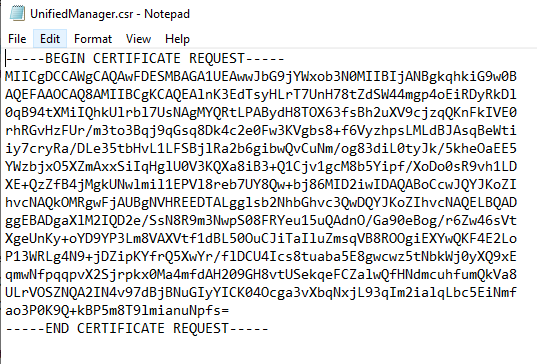
Open the UnifiedManager.csr in notepad
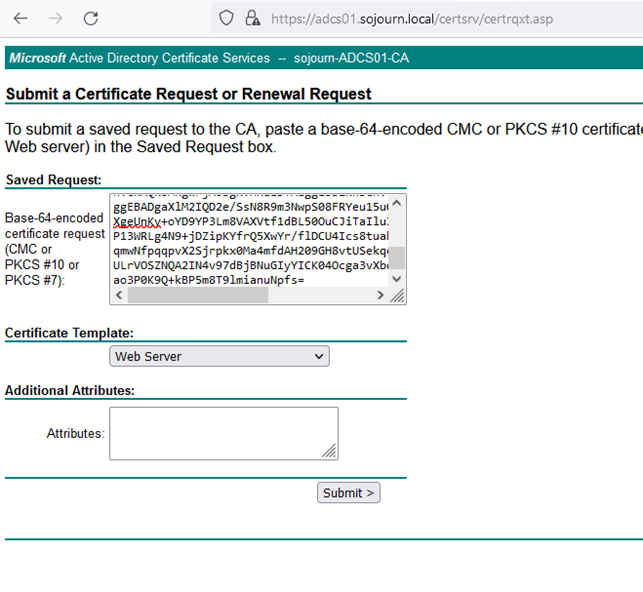
Browse to you CA website (mine is https://adcs01.sojourn.local/certsrv) and submit an advanced certificate request.
Download the chain in DER encoding and you get a certnew.p7b file.

We need to convert it to PEM as that is the format AIQ supports.
I use my ubuntu linux workstation to do convert from DER to PEM.
ronnie@ubntsojourn01:~$ openssl pkcs7 -inform DER -print_certs -in certnew.p7b -out aiq.sojourn.local.pem
When I tried to load the PEM file, I got this error.
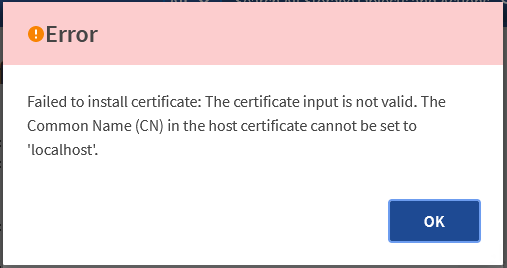
This turned out to be because, for some reason the hostname of my ActiveIQ was set to “UnifiedManager” and the signing request was create with “localhost”.
It should have been a hint that the self-signed certificate was created to “localhost” and not the FQDN.
Even though I am using the virtual appliance version changing the hostname is done like if it had been deployed in a linux machine.
First enable ERDS from the console
ssh to the machine. Rename using hostnamectl
diag@UnifiedManager:~$ sudo hostnamectl set-hostname aiq.sojourn.local
Recreate the self signed certificate
diag@UnifiedManager:~$ sudo /opt/netapp/essentials/bin/cert.sh create 2023-04-17 11:10:20 INFO: Creating certificate with default parameters in keystore: '/opt/netapp/data/ocie/server.keystore' 2023-04-17 11:10:20 INFO: At this point Hostname is: aiq.sojourn.local IP Address is: 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000 link/ether 00:50:56:9f:b2:a2 brd ff:ff:ff:ff:ff:ff inet 192.168.41.13/24 brd 192.168.41.255 scope global eth0 valid_lft forever preferred_lft forever inet6 fe80::250:56ff:fe9f:b2a2/64 scope link valid_lft forever preferred_lft forever 2023-04-17 11:10:20 INFO: Creating a copy of keystore: '/opt/netapp/data/ocie/server.keystore' in '/opt/netapp/essentials/jboss/server/onaro/cert' And then reboot the machine.
When AIQ is up after the reboot, check the self-signed certificate. Here I found my second problem.
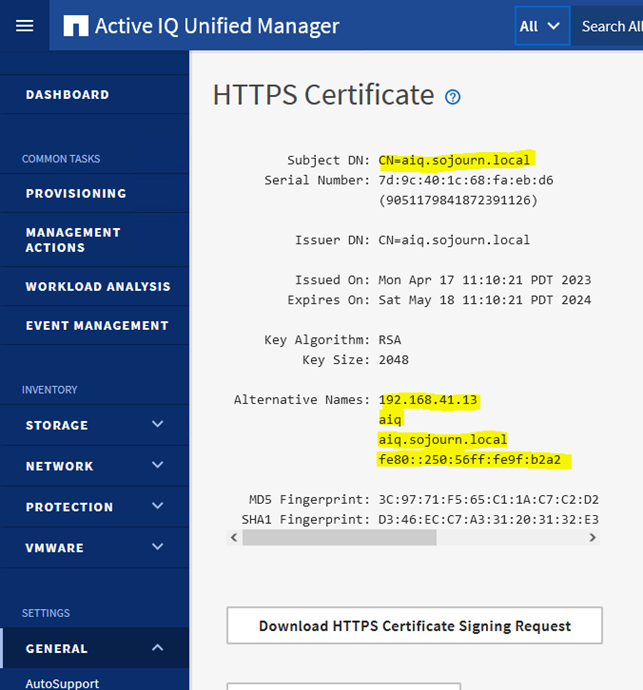
The new self-signed certificate was create with ip in the alternative name. This is not supported in when importing a new signed certificate. NetApp has a KB about it:
So after changing that, and another reboot our self-signed certificate looks like this. (Remember to check the box ”Exclude Local Identifying Information” or you might be rebooting twice).
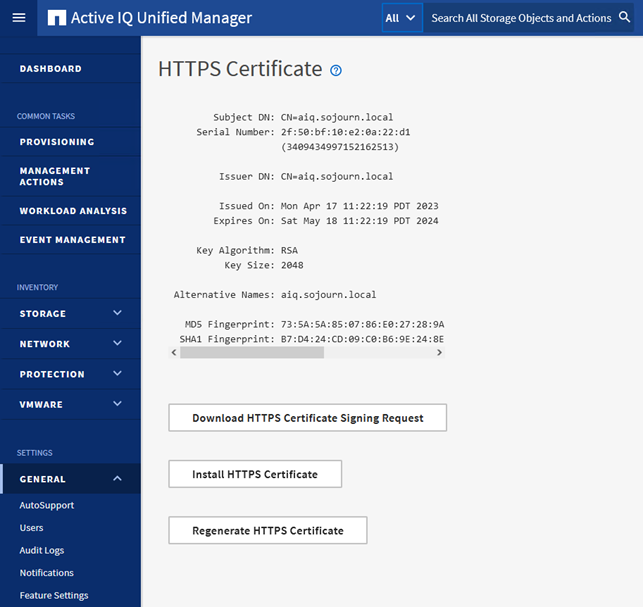
I was now ready to create a new signing request and try again. Go through all the steps again.
- Request certificate from https://adcs01.sojourn.local/certsrv
- Download the complete DER chain
- Convert the .p7b file to PEM
- Upload the PEM to AIQ
And reboot again.
I was once again able to use Chrome